Have you ever been seen your website’s search results showing Japanese text? If yes then, you might have been the victim of the Japanese Keyword Hack. Recently, I have been encountered with a massive Japanese keyword hack on my own website. And that’s not my first time, I have been faced such circumstances many times in my last 10 years of career as an SEO professional. But, I knew how to fix this Japanese keywords hack. To find out what it is and how to fix it, lets read on!
What is a Japanese Keyword Hack or Japanese SEO Spam?
The “Japanese Keyword Hack” or “Japanese SEO Spam” is a type of SEO spam attack where hackers injects a malicious malware that creates auto-generated Japanese text and keywords into your website’s pages, titles, and descriptions, also generated thousands of unwanted webpages aiming to manipulate search engine rankings for their own benefit, often by linking to scam sites.
Most of times, when you use CMS platforms like WordPress, OpenCart, Magento, or Drupal, your site can get hacked with Japanese SEO spam. These spam pages promote fake products using your site’s links to boost their own traffic and sales.
How to Identify this type of Japanese Keyword Hack?
The Japanese keyword hack is a type of website hack where random new pages filled with Japanese text suddenly appear on your site. These pages are usually hidden in weird-looking folders like yourwebsite.com/ltjmnjp/341.html. Hackers use these pages to add affiliate links that lead to fake online stores selling counterfeit brand products. These spammy pages often show up in Google search results and can harm your site’s reputation.
Here are different ways how to Identify the Japanese Keyword Hack is really infected on your website or not:
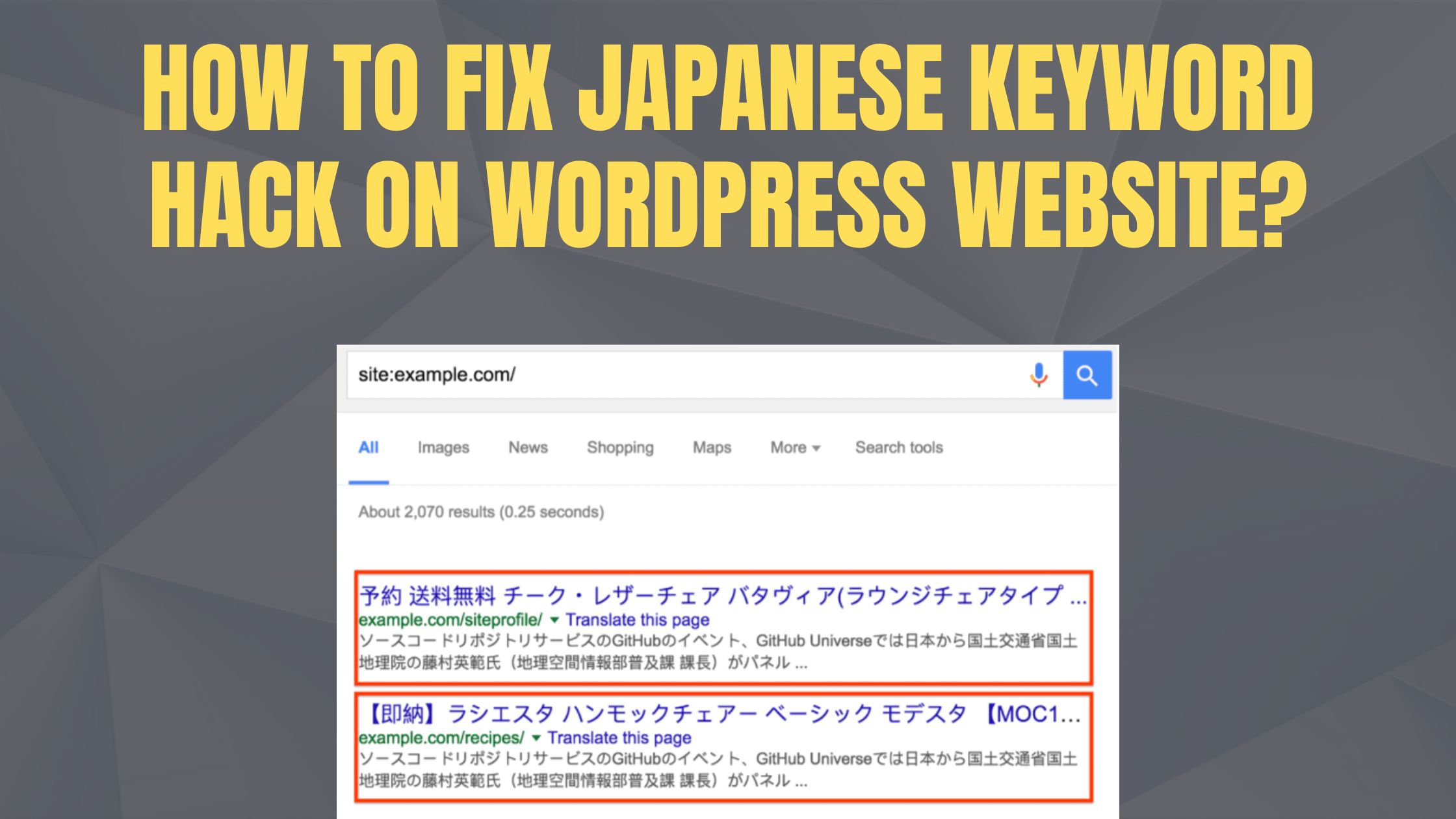
- Check Google Search Results: Search
site:yourdomain.comon Google. If you see Japanese titles, descriptions, or product pages that don’t belong to your site — that’s a red flag.
Here’s how I checked my site was infected by Japanese keywords as showing in the screenshot below 👇🏿
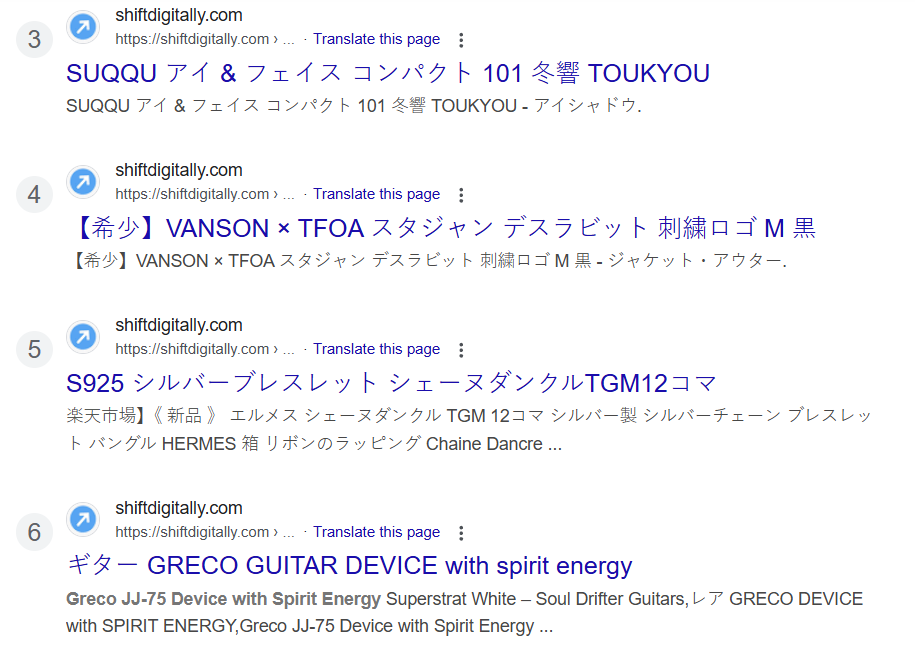
- Look for Weird URLs: Japanese spam pages are often hidden in strange folders like:
yourdomain.com/abcdxy1/341.html. These directories are randomly generated. You can check your Performance tab section and select Pages in Google search Console as I found in my search console screenshot shared 👇🏿

- Sudden Drop or Spike in Traffic: Check Google Search Console or Google Analytics. A sudden change in traffic (especially from Japan or unusual sources) can be a sign of Japanese keyword attack.
- Check how many pages of your site show up on Google: If your website usually has around 20 webpages in search results, but suddenly it shows hundreds of thousands, that’s a strong sign it’s been hacked. The Japanese keyword hack can secretly add tons of spam webpages to your site without you knowing.

- Google Search Console Warnings: Go to Security Issues under your GSC dashboard. It might show warnings like “Hacked content detected” or “URL contains spam”.

- Check for Unfamiliar Users or Plugins: Log in to your CMS (WordPress, Magento, etc.). Look for suspicious admin users or unknown plugins/themes.
- One or more .htaccess files found in File Manager: There may be more than one .htaccess file that is the cause of the redirects, if your visitors are experiencing them. Your website should only have one .htaccess file.
- Multiple XML sitemap found in Google Search Console: There may be more than one XML Sitemap files exists. You can check your Google search console sitemap section if multiple unwanted XML sitemaps found would be another root cause.
- Use an SEO Audit Tool: Tools like Ahrefs, SEMrush, or Screaming Frog can help find hidden spam pages. Look for Japanese keywords or pages with odd titles/meta data.
- Scan Your Website: Use security tools like Sucuri, SiteCheck or Wordfence (for WordPress) to scan your site for malware or injected code.
How to Fix the Japanese Keyword Hack
Here is the simplest way to how you can fix or remove these Japanese keyword hack and you’ll also know what I did for my site.
- Backup your website before cleaning: Before you start cleaning up malware from your WordPress site, make sure to take a full backup. If anything goes wrong during the process, you’ll be able to restore your site. Save the backup as a compressed .zip file to keep everything in one place and easy to use. I did the same first.
- Run a Malware Scan: Check your web server for any malware or suspicious files. Here’s how you can do it:
- If your hosting uses cPanel, look for a tool called “Virus Scanner” — it’s usually built-in and easy to run.
- You can also use these free malware scanners:
These tools will scan your site and let you know if anything shady is going on. But, keep in mind that these scanners can’t guarantee that they will identify every type of problematic content.
- Remove any newly created user accounts in the Google Search Console:
Go to the “Users and Property Owners” section in Google Search Console. This is where you can check who has access to your site. If you see any users you don’t recognize — especially Gmail accounts you didn’t add — remove them right away. Hackers often add themselves as admins so they can mess with your site’s settings, like your sitemap or location targeting.
In my case, a hacker verified access using an HTML file they placed in my website’s root folder. First, I deleted that file. Then, I went to Search Console and removed permanently their user access from the Users and Property Owners tab.
As you can see below screenshot from Ownership History, that the verification record was deleted.

To remove the dynamically generated verification token from your .htaccess file, follow these steps:
- Checkout your .htaccess file in Root folder
Step 1: Find the .htaccess File
Look for the .htaccess file in your website’s root folder. If you’re using WordPress, Joomla, or Drupal, just Google something like “.htaccess file location WordPress” to help you find it.
Important: .htaccess is a hidden file, so make sure to enable “Show hidden files” in your file manager or FTP client.
Sometimes, you might find more than one .htaccess file in different folders — make a list of all of them.
Step 2: Replace with Clean or Default Files
Once you’ve found the .htaccess files:
- Replace them with clean/default versions. You can find these by searching online for:
“Default .htaccess file [Your CMS Name]” (e.g., WordPress or Joomla). - If you’ve never customized
.htaccess, and there’s no default available, the one on your site might be malicious. - In that case, download a copy to your computer (just in case), then delete it from your site.
In my case, I got found 3 different .htaccess files in my root folder which is public_html then I deleted those injected .htaccess files and left the original one in the folder.
- Check your root folder for suspicious files
All your WordPress files — including the core, plugins, and themes — are usually stored in the public_html folder. This is your website’s main root folder. Sometimes, hackers drop malicious files here that seem normal but are actually full of spam links or harmful code.
Not all unknown files are dangerous, but it’s always a good idea to check them.
In my case, I found two suspicious files named products.php and details.php in the root folder. These files contained thousands of spam URLs. I deleted both files permanently using the File Manager in my web hosting panel.
After deleting those malicious files, I went to Google Search Console → Removals and submitted their URLs to be removed from search results. I added the exact file URLs (like yourwebsite.com/products.php and yourwebsite.com/details.php) so Google would stop showing them. Since those pages now return a 404 error, Google will eventually drop them from its index the next time it crawls the site.

Don’t stress about checking every single PHP file in the root folder— you don’t need to. Instead, make a list of files that look suspicious and focus on those first. Here’s how you can spot them:
Sort files by size. If you see any PHP files that are unusually large, they could be hiding malicious code.
If you’ve reinstalled your CMS (like WordPress), ignore the default files. Only check the ones that don’t belong to the original CMS — those are more likely to be suspicious.
Sort files by “Last Modified Date” in your File Manager. Look for any that were changed around the time you noticed the hack.
6. Check your XML Sitemap in Google Search Console:
Hackers sometimes change your sitemap or add new ones to get their spam pages on Google faster.
If you had a sitemap before, open it and check for any strange or spammy links, delete them if you find any.
Also, if you see sitemap files you didn’t add yourself, open them. If they only contain spammy links, go ahead and remove those files.
In my case, I found 3 different XML Sitemap files which was submitted unauthorized in my Google search console. So, I deleted those sitemaps and update with my fresh XML sitemap file belongs to the site.
Check your Robots.txt file
Just like you check your XML sitemap, you should also take a look at your robots.txt file. Hackers sometimes edit this file and add links to their own sitemap files. Go to the robots.txt section in Google Search Console settings. There, you can see the latest version Google fetched from your site. If you see anything unusual or any sitemap URLs you didn’t add, remove them right away.

I also found those sitemap links in the robots.txt too, So, I deleted that robots.txt file and update with the new one. And resubmitted to the Google search console.
- Check the plugins and themes
After uploading the cleaned files and database, and your site is loading — that’s a good indication!
Now, go through each page to make sure everything works properly.
To be safe, you can disable the entire plugins folder, then enable one plugin at a time to check if anything breaks. Do the same with your themes — test one at a time to make sure your site runs smoothly. Remove any plugin or unused themes if its not necessary in use. And keep both up to date on your website.
If you were using nulled plugins or themes before, delete them completely. They’re risky and often contain hidden malware or backdoors that hackers use to get into your site again.
I deleted unwanted themes and plugin with was not used. And update both theme and plugins to their latest version.
7. Check Your Uploads Folder in your servers File Manager
Go to your wp-content/uploads folder and look for any unusual files — especially ones ending in .php, .js, or .ico. These don’t belong in the uploads folder.
If you find files like that, open them and look for strange code with words like:base64_decode, eval, strrev, gzinflate, or rot13.
These are signs the file might be malicious, so it’s best to delete them right away.
8. Check whether your site is clean
Once you’ve done all the hacked files cleaned, it’s time to check if it worked.
Remember those spammy or gibberish pages you found earlier? Now check the Page Indexing section in Search Console to check them again.
If Google shows a “Not Found” (404) response for large number of webpages, then congratulations that’s a good sign — it means those pages are gone. Now you can move on to fixing any vulnerabilities on your site to prevent future hacks.
How to Prevent Japanese SEO hacked again?
Now that you’ve removed the Japanese keyword hack, the hardest part is done — great job! 🙌
If you used a tool like MalCare, it likely cleared out both the malware and hidden backdoors.
But you’re not completely out of the woods yet. It’s important to tighten your website’s security and undo any damage left behind.
🛡️ Here’s what you should do next to protect your site:
- Install a WordPress security plugin that scans daily, auto-cleans malware, and includes a firewall.
- Change all passwords — for WordPress users, your database, and SFTP.
- Force reset all user accounts to be extra safe.
- Delete unused plugins or themes you’re not actively using.
- Enable SSL (HTTPS) to keep your site more secure.
- Set up automatic backups — they can save you if anything goes wrong again.
✅ Remember: Website security is not a one-time thing. It’s needs regular security.
Make it a habit to regularly review your users, activity logs, and passwords to keep your site safe in the long run.
Now you understood, how crucial is to secure your website from such malware attack and learned how to get rid for this Japanese keyword attack and its prevention for the future. And knew that how I removed this Japanese keyword attack from my own website.
I hope you found this Japanese keyword hack removal guide helpful and its easy to follow.
If you have any questions or need a hand, feel free to reach out — I’m always here to help!